
Satellite internet infrastructure, while revolutionary, underscores critical cybersecurity responsibilities. MicroSec Researchers recently identified and responsibly disclosed an unintended exposure involving a Starlink customer terminal. This disclosure explores how misconfigured third-party equipment inadvertently exposed a limited set of internal gRPC commands, the potential implications, and necessary security best practices.
During routine web reconnaissance, MicroSec Researchers discovered an exposed IP address via the Censys search engine. The IP initially presented open ports that appeared innocuous; however, port 9201 exhibited atypical behavior. Upon detailed examination, researchers found that modifying the HTTP Host header to `192.168.100.1:9201` activated responses indicative of an internal gRPC service.
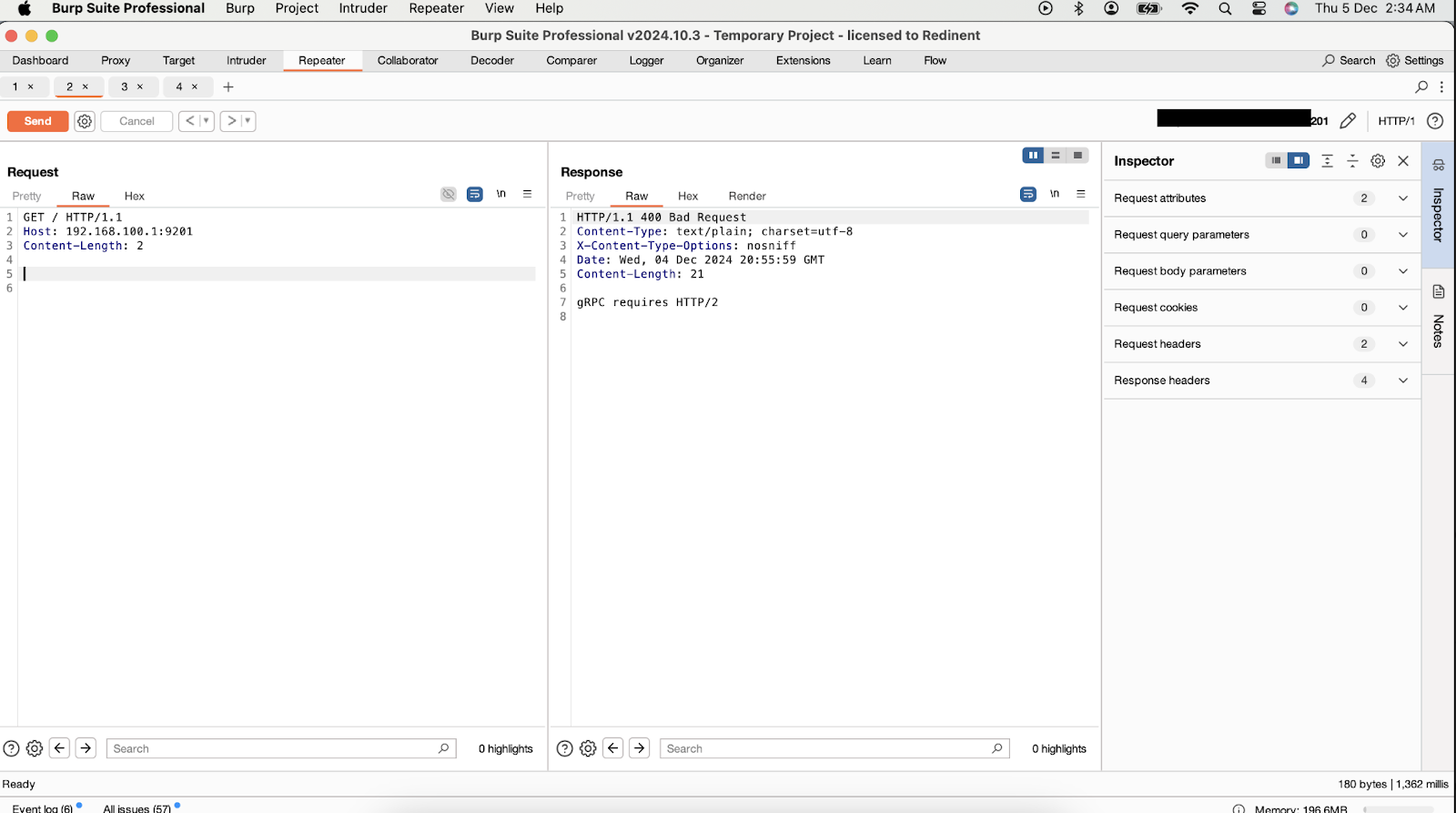
Further investigation led researchers to the publicly available GitHub repository, `starlink-rs`, specifically designed to interact with Starlink gRPC services. Using this tool, researchers confirmed successful execution of the built-in command `SpaceX.API.Device.Device` via the exposed IP address. This interaction positively identified the device as a Starlink router, demonstrating unauthorized yet limited command execution capabilities.
To reinforce findings, researchers initiated a Telnet connection on port 22, receiving the explicit banner:
SpaceX User Terminal.
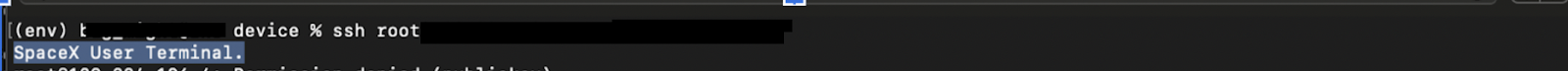
This banner explicitly confirmed the exposed IP was a genuine Starlink customer terminal.
Root Cause Analysis:
The MicroSec Researchers' disclosure prompted a quick response from SpaceX, which clarified that the exposed terminal was customer-owned. SpaceX attributed the exposure entirely to the customer's misconfigured third-party routing equipment. The misconfiguration resulted in WAN-to-LAN traffic forwarding, unintentionally exposing internal services, including the Starlink terminal’s internal gRPC interface.
SpaceX confirmed:
* The gRPC service intentionally offers limited unauthenticated commands restricted to local networks.
* No sensitive configuration or modification commands were exposed.
* Authentication remains necessary for any critical command execution.
Following the responsible disclosure by MicroSec Researchers, SpaceX immediately contacted the affected customer and rectified the misconfiguration.
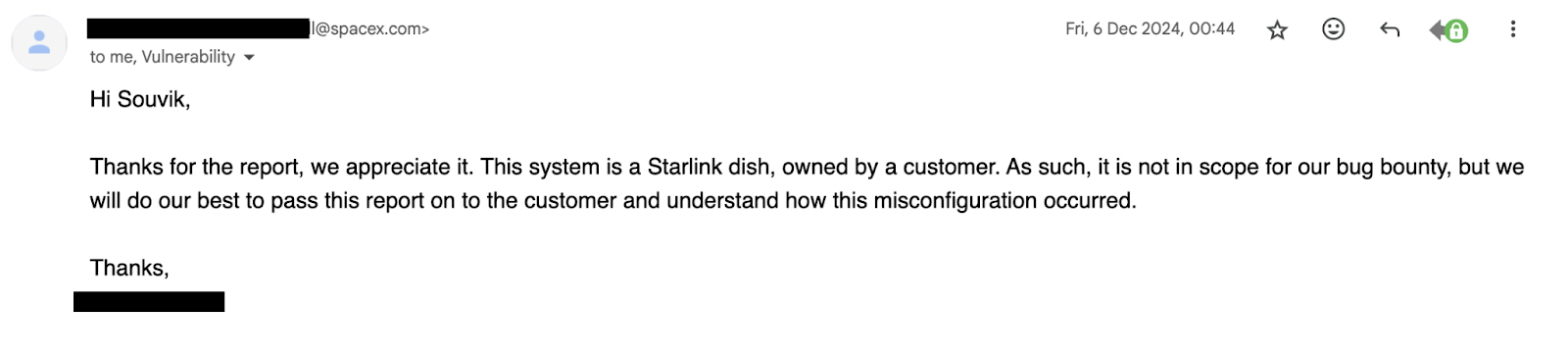
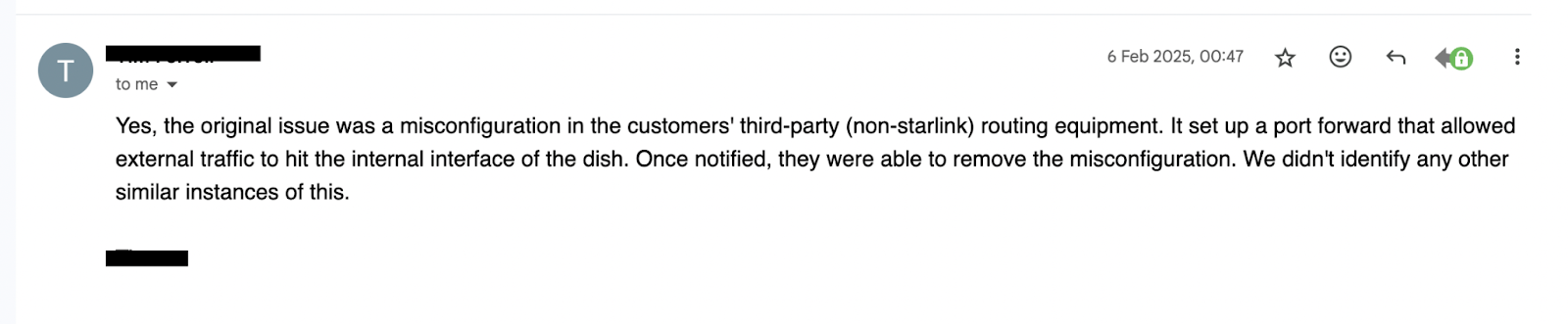
MicroSec Researchers explored how attackers might exploit such misconfigurations:
Step 1: Identifying Exposed Devices
Attackers could utilize sources like CVE reports and DEFCON presentations mentioning "Starlink" banners and gRPC on port 9201.
From the blog, we can extract key indicators:
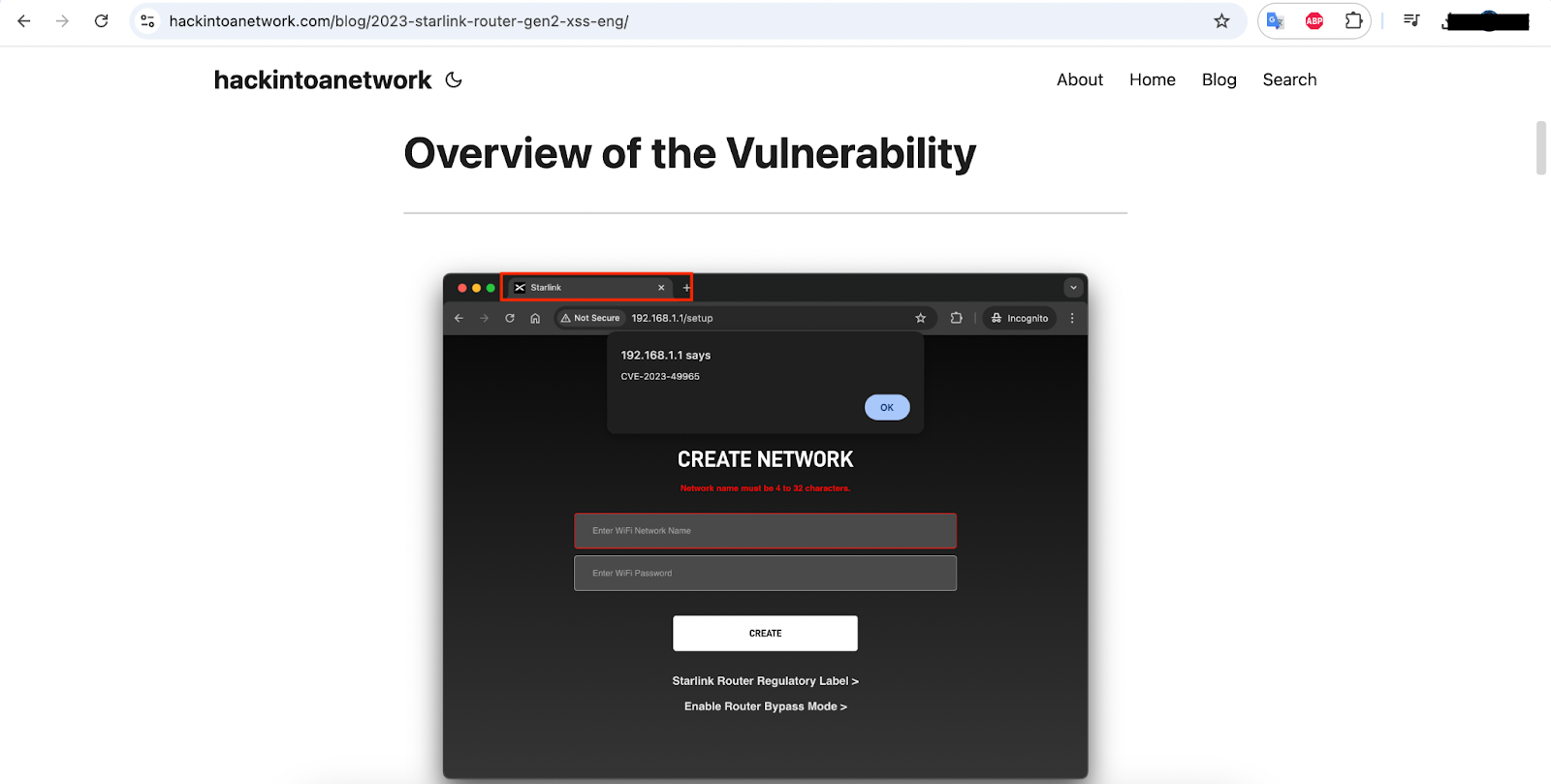
• The HTTP login page title contains "Starlink".
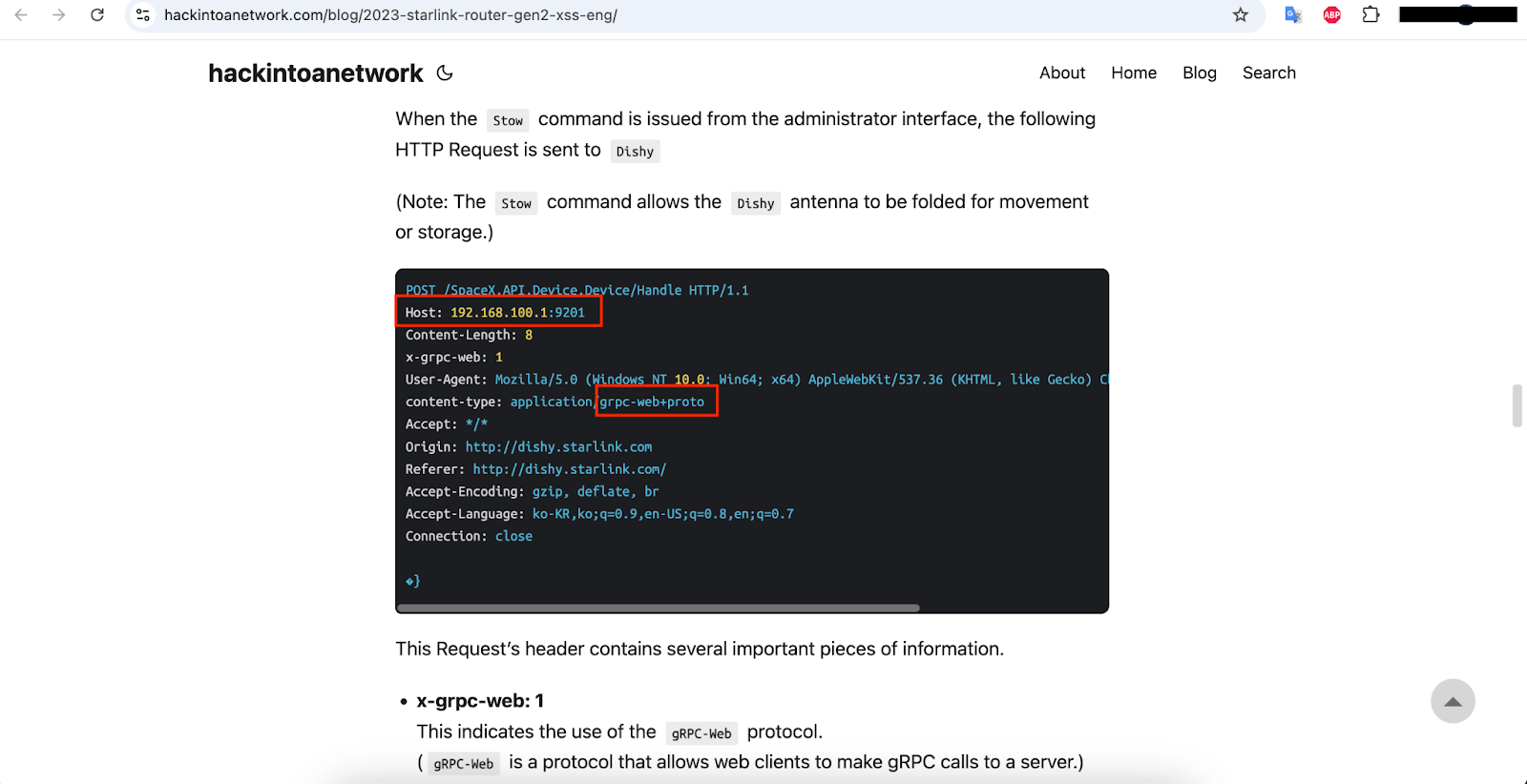
• The gRPC service is running on port 9201.
analyzing a DEFCON talk on Starlink routers (YouTube Link), we discover another critical detail:
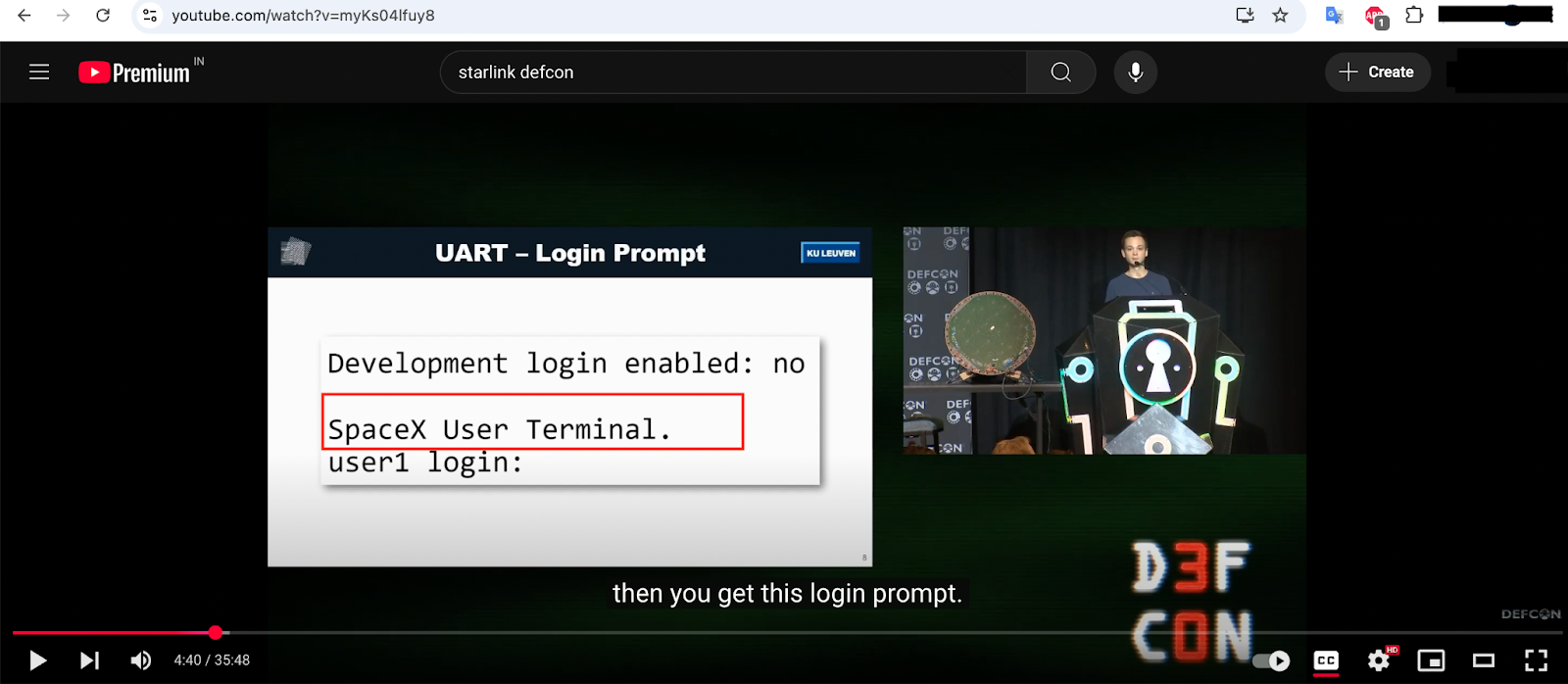
• The terminal banner includes "SpaceX User Terminal."
Using this information, an attacker can create a search query for Censys to identify exposed devices:
services.http.response.html_title="Starlink" and "SpaceX User Terminal" and services.port=9201
This query would effectively pinpoint similarly misconfigured devices.
Step 2: Exploitation Using Public Tools:
After identification, attackers might leverage the `starlink-rs` repository tool to execute the available limited commands. While limited in nature, the availability of these internal commands presents unnecessary exposure and potential reconnaissance risk.
Security Impact Analysis:
• Unauthorized control over customer devices.
• Potential data leaks due to exposed internal services.
• Service disruption risks if an attacker exploits the flaw maliciously.
MicroSec Researchers provided clear recommendations to mitigate such incidents:
* Avoid third-party routing equipment unless necessary, ensuring strict firewall configurations.
* Eliminate unnecessary WAN-to-LAN port forwarding.
* Conduct regular audits of network settings to proactively detect and rectify misconfigurations.
* Deploy appropriate cybersecurity monitoring and detection tools, like MicroIDS, to immediately detect and alert users if unauthorized access attempts to their Starlink device occur.
This exposure was responsibly discovered and disclosed by MicroSec's Lead Security Researcher, Souvik Kandar. SpaceX promptly acknowledged, clarified, and facilitated the rectification of the identified misconfiguration, exemplifying effective industry collaboration in cybersecurity.
This research was responsibly conducted and disclosed by MicroSec Researchers as part of ongoing efforts to enhance cybersecurity awareness. SpaceX confirmed that the reported issue resulted from third-party equipment misconfiguration and did not involve vulnerabilities in SpaceX or Starlink systems. MicroSec remains committed to collaborative industry efforts to identify and mitigate cybersecurity risks in emerging technological infrastructures.