Ensuring cybersecurity compliance in OT and IoT environments is far from straightforward. Organizations face fragmented standards, manual and error-prone processes, and little clarity on what to fix first. The result is wasted time, rising costs, and increased exposure to cyber and regulatory risks.
Most regulatory frameworks are very lengthy and hard to understand for a cybersecurity novice. Businesses often just try to get a tick, while actually keeping loopholes in their cybersecurity architecture.
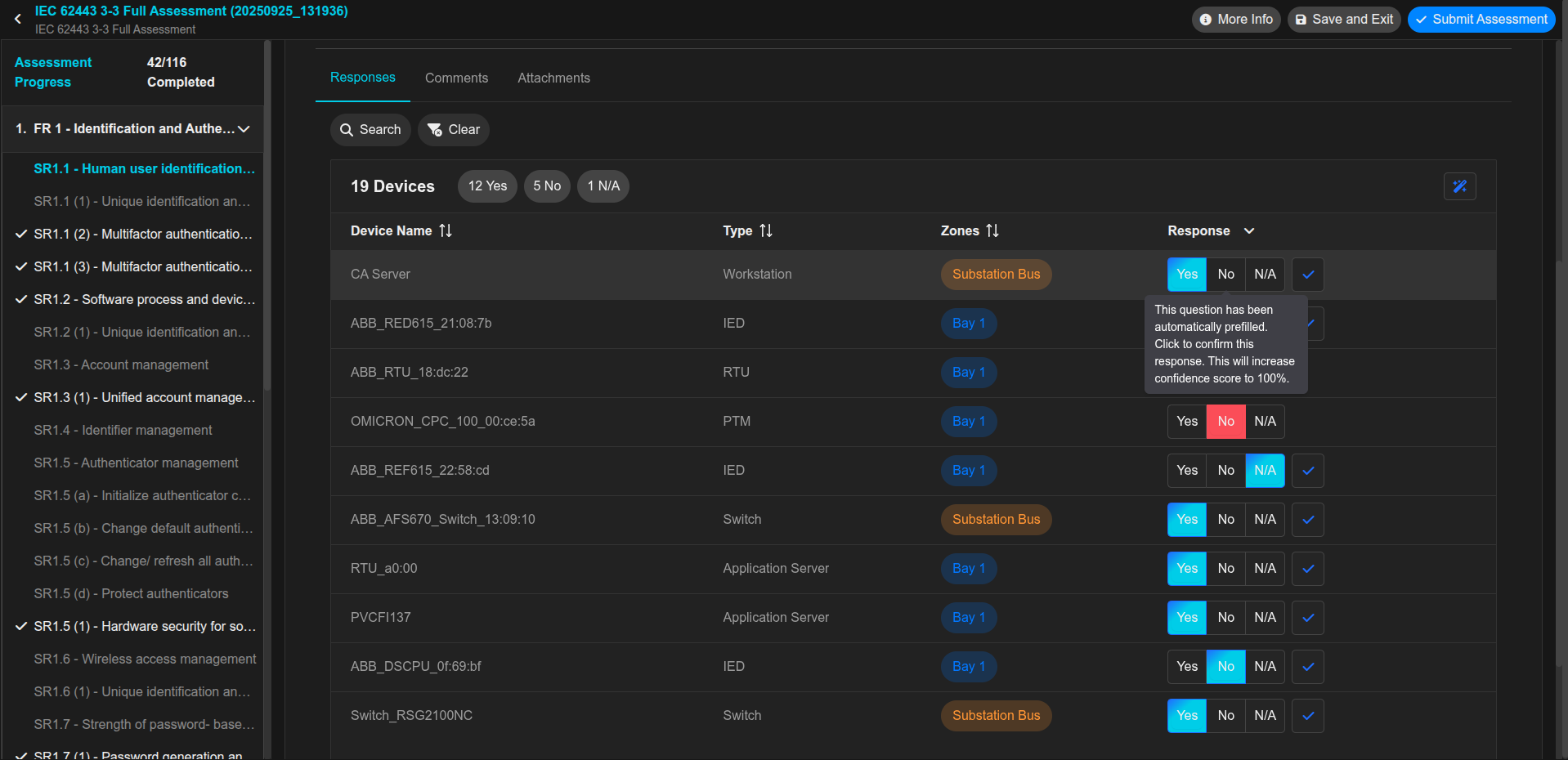
Traditional cybersecurity assessments are manual, tedious, and slow. They can be prone to errors or incorrectness, whether intentional or unintentional, leading to inaccurate assessments and gaps in security.
Even after assessments, businesses lack clear priorities. Generic tools miss industry nuances, create wasted effort, and overwhelm teams with false positives instead of guidance.
CyberAssessor turns complex compliance into a clear, automated process while ensuring an end-to-end compliance journey. Powered by AI, it continuously maps your OT and IoT systems against standards like IEC 62443, IACS UR E26/E27, NIST, and more. It cuts down manual effort, reduces false positives, and delivers audit-ready reports with prioritized actions so you can address what matters most, faster and at lower cost.


Reduce false positives to less than 5% with federated AI models trained for OT/IoT environments
IEC 62443, IACS UR E26/E27, NIST, and customizable corporate baselines
Go beyond one-time audits and monitor compliance posture dynamically as systems evolve
Receive prioritized remediation playbooks mapped directly to controls
Assess in air-gapped, hybrid, or cloud environments
Natively connects with MicroIDS Monitoring Suite and LCMS Protection Suite for unified visibility and Zero-Trust
MicroIDS supports a wide variety of cybersecurity standards in our CyberAssessor platform, from global frameworks like IEC 62443 to industry-specific ones such as IACS UR E26. It even allows for customized assessments to meet unique compliance needs, while also covering both local and international regulatory requirements. This ensures your organization stays compliant no matter the industry or jurisdiction.






CyberAssessor provides automated compliance assessments based on on-the-ground truth of discovered device information.
This ensures accurate and up-to-date compliance status, minimizing manual errors and oversights.

CyberAssessor offers clear, prioritized mitigation strategies tailored to your specific compliance gaps.
This guidance helps businesses take decisive actions to address vulnerabilities effectively, ensuring a streamlined path to achieving cybersecurity targets.

CyberAssessor generates detailed reports that are not only useful for internal audits and documentation but are also recognized as proof of compliance by certification bodies. This ensures that your compliance efforts are both thorough and verifiable.

Schedule a free assessment today.
For all other inquiries, please reach out to info@usec.io.
MicroSec offers two platforms:
Protection Suite to secure your IoT devices & network end-to-end and Monitoring Suite to detect & stop threats on your assets instantly.
Protect and manage all of your devices and networks with advanced cybersecurity device management capabilities & lightweight PKI
Assess and guard your devices and networks against zero day attacks with ML anomaly detection and instant remediation

LEGACY SOLUTIONS
PROTECTION SUITE